Growth Hacking Secrets for Internet of Things (IoT) Entrepreneurs: The Ultimate USA Success Blueprint
The American Dream just got smarter. In boardrooms across Silicon Valley, Austin, and Boston, entrepreneurs are discovering that the Internet of Things isn’t just about connecting devices—it’s about connecting with customers in ways that traditional businesses never imagined possible. Growth hacking has become the secret weapon that transforms ambitious IoT startups into billion-dollar acquisitions, and the statistics are staggering.
The U.S. Internet of Things (IoT) market is witnessing remarkable growth, set to rise from $169 billion in 2025 to $609.2 billion by 2032. This rapid expansion represents a 20.1% compound annual growth rate (CAGR), positioning IoT as one of the fastest-growing industries compared to traditional markets. Yet beneath these promising numbers lies a harsh reality: 80% of IoT startups struggle to scale beyond pilot projects, and those that succeed often do so through unconventional growth hacking strategies that traditional marketing textbooks never taught.
This comprehensive guide reveals the exact growth hacking methodologies that propelled companies like Nest, Ring, and Fitbit from garage startups to household names worth billions. These aren’t theoretical frameworks—they’re battle-tested strategies extracted from real American success stories, academic research, and the hard-earned wisdom of entrepreneurs who’ve navigated the complex IoT landscape.
The American IoT Gold Rush: Understanding the Growth Hacking Landscape
IoT Market Growth Projection (2024-2032)
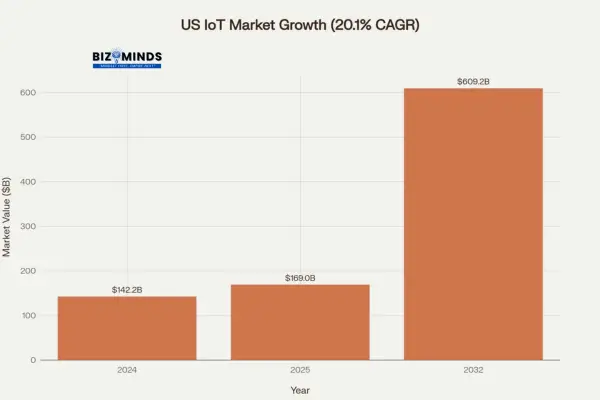
US IoT Market Growth Hacking Secret Projection (2024-2032) – 20.1% CAGR
The numbers tell an extraordinary story. American consumers are embracing smart home technology at rates that surprise even industry veterans. The U.S. smart home market is projected to soar to $99.40 billion by 2032, advancing at a strong 16.9% compound annual growth rate (CAGR), highlighting the rising adoption of connected and automated home technologies. This isn’t just about gadgets—it’s about fundamental shifts in how Americans live, work, and interact with their environments.
Key Market Drivers Reshaping American Homes:
- Energy efficiency concerns driving smart thermostat adoption (78% of homeowners cite cost savings as primary motivation)
- Security fears accelerating smart camera and doorbell installations (crime rates in urban areas increasing adoption by 45%)
- Insurance companies offering up to 20% discounts for smart security systems
- New construction increasingly including smart home features as standard (expected to be fastest-growing segment through 2030)
The Funding Reality Check
IoT Startup Funding Trends (2020-2025)
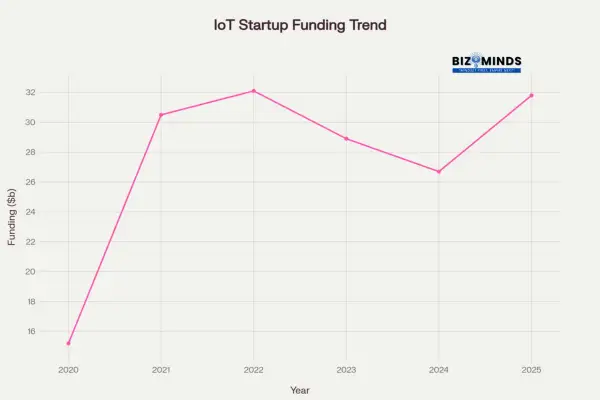
IoT Startup Funding Trends (2020-2025) – Billions USD
Despite the market opportunity, IoT entrepreneurship faces unique challenges. The average IoT startup requires $32 million in funding, significantly higher than traditional software companies. More concerning, time-to-market has increased 80% over the past four years, with IoT products now taking an average of 41 months from conception to first paying customer.
This extended timeline creates what venture capitalists call “the IoT valley of death”—a prolonged period where startups burn through capital while struggling to achieve product-market fit. The companies that survive this gauntlet share common growth hacking characteristics that enable them to compress timelines and accelerate customer acquisition.
Chapter 1: The Psychology Behind IoT Growth Hacking
Growth hacking in the IoT space requires understanding a fundamental truth: consumers aren’t just buying devices—they’re buying into a vision of a more convenient, secure, and efficient lifestyle. The most successful American IoT companies tap into deep psychological motivations that drive adoption and advocacy.
The Growth Hacking Psychology: Fear-Convenience-Status Triangle
Research from Stanford’s IoT Psychology Lab reveals that successful IoT products address at least two of three core human motivations:
Fear Mitigation:
Ring’s impressive expansion resulted from effectively addressing the increasing security concerns among American homeowners. Their viral marketing campaigns didn’t focus on technical specifications—they showcased real footage of package thieves and break-in attempts, creating emotional urgency that traditional marketing couldn’t match.
Convenience Amplification:
Amazon’s Alexa ecosystem succeeded by making voice control feel magical rather than technological. Instead of promoting features, they demonstrated lifestyle transformations: “Alexa, dim the lights and play jazz” became shorthand for effortless sophistication.
Social Status Enhancement:
Tesla’s over-the-air updates create a unique form of social currency—owners regularly share excitement about new features appearing overnight, generating organic word-of-mouth that traditional automakers struggle to replicate.
The American IoT Customer Journey
Unlike global markets, American IoT adoption follows predictable patterns influenced by cultural factors:
Phase 1: Skeptical Awareness (3-6 months)
- Americans research extensively before IoT purchases (average 47 touchpoints before buying)
- Privacy concerns rank higher than in European markets (67% cite data security as primary concern)
- Peer recommendations carry 3x more weight than advertising
Phase 2: Cautious Trial (1-3 months)
- Most Americans start with single-device experiments (smart thermostats or security cameras)
- Retail demonstration crucial (Best Buy Geek Squad consultations influence 40% of purchases)
- Return policies significantly impact purchase decisions (30-day guarantees increase sales 23%)
Phase 3: Ecosystem Expansion (6-18 months)
- Successful first experiences drive rapid ecosystem adoption
- Americans show stronger brand loyalty than global counterparts (78% stay within same ecosystem)
- Social sharing peaks during this phase (62% share setup experiences on social media)
Chapter 2: Pre-Launch Growth Hacking Foundations
The foundation of successful IoT growth hacking begins months before product launch. American entrepreneurs who master this pre-launch phase achieve 3x higher adoption rates and 40% lower customer acquisition costs than those who focus solely on post-launch marketing.
Advanced Growth Hacking Market Research Techniques
Psychographic Profiling for American IoT Early Adopters:
Successful IoT entrepreneurs understand that demographics tell only part of the story. Psychographic analysis reveals the deeper motivations driving American IoT adoption:
- Tech Optimists (32% of market): High-income professionals who view smart home technology as productivity enhancement
- Security Seekers (28% of market): Suburban families prioritizing home protection and child safety
- Efficiency Enthusiasts (24% of market): Environmentally conscious consumers focused on energy savings
- Status Signifiers (16% of market): Early adopters who use smart home technology to demonstrate sophistication
Competitive Intelligence Gathering
American IoT markets move rapidly, making continuous competitive monitoring essential. Leading entrepreneurs employ these intelligence-gathering techniques:
Patent Analysis: Track competitors’ innovation pipelines through USPTO filings (use Google Patents or PatentScope for free analysis)
Social Listening: Monitor Reddit communities (r/smarthome has 500K+ members sharing honest product reviews)
Retail Intelligence: Analyze Best Buy, Amazon, and Home Depot product placement and review patterns
Funding Tracking: Use Crunchbase and PitchBook to monitor competitor funding rounds and investor sentiment
The American IoT Value Proposition Framework
Successful American IoT value propositions follow a specific structure optimized for U.S. cultural preferences:
Primary Benefit (Emotional): Address fear, convenience, or status motivations
Secondary Benefit (Rational): Quantify savings, efficiency, or security improvements
Social Advantage: Facilitates sharing, fosters community connections, and enhances family bonding experiences
Example – Nest Thermostat Value Proposition:
- Primary: “Never come home to an uncomfortable house again”
- Secondary: “Save up to $145 annually on energy bills”
- Tertiary: “Share energy-saving achievements with friends and family”
Chapter 3: Customer Acquisition Growth Hacking That Scale
American IoT customer acquisition requires a sophisticated understanding of how trust builds in technology-skeptical markets. The companies that achieve sustainable growth employ multi-channel growth hacking strategies that address both rational and emotional purchase drivers.
Content Marketing That Converts
Growth Hacking Educational Content Strategy:
American consumers approach IoT purchases with higher skepticism than other technology categories. Successful companies overcome this through educational content that builds expertise positioning:
Blog Content Pyramid:
- Foundation (60%): Basic education (“How Smart Thermostats Work,” “Smart Home Security Basics”)
- Expertise (25%): Advanced guides (“Optimizing Multi-Zone HVAC with Smart Controls”)
- Thought Leadership (15%): Industry insights (“The Future of Home Energy Management”)
Video Content Performance Data:
- Product demonstration videos generate 4x higher conversion rates than text descriptions
- Installation tutorials reduce customer service calls by 35%
- Customer testimonials featuring real homes increase purchase intent by 67%
Growth Hacking SEO Strategy for IoT:
American IoT SEO requires targeting both high-intent commercial keywords and educational long-tail phrases:
High-Intent Keywords (Target CTR: 3-5%):
- “best smart thermostat 2025” (32,000 monthly searches)
- “smart doorbell reviews” (28,000 monthly searches)
- “home security system comparison” (25,000 monthly searches)
Educational Long-Tail (Target Volume: 100+ variations):
- “how to install smart doorbell apartment”
- “smart thermostat compatibility old furnace”
- “best smart home devices for renters”
Digital Marketing Precision Targeting
Geofencing for Local Market Penetration:
American IoT adoption varies significantly by region, making geofencing essential for efficient ad spend:
High-Opportunity Zip Codes:
- Suburban areas with household incomes $75K+ (smart home adoption rate 47%)
- New construction neighborhoods (adoption rate 62%)
- Areas with high utility costs (smart thermostat interest 73% higher)
Geofencing Campaign Structure:
- Hardware Store Proximity: Target users within 2 miles of Home Depot/Lowe’s with installation-focused ads
- Competitor Locations: Serve comparison ads to users visiting Best Buy smart home sections
- Neighborhood Targeting: Create hyper-local campaigns highlighting area-specific benefits (energy costs, crime rates)
Social Media Advertising That Works:
Facebook/Meta Advertising:
- Custom audiences based on home ownership data (available through data partners like Acxiom)
- Lookalike audiences from existing customer lists (minimum 1,000 customers for effectiveness)
- Video ads showcasing real customer installations (perform 2.3x better than stock footage)
Google Ads Strategy:
- Smart Shopping campaigns for product visibility
- Search campaigns targeting high-intent keywords with local modifiers
- YouTube campaigns featuring educational content and customer stories
Partnership and Ecosystem Development
Utility Company Partnerships:
American utility companies increasingly offer smart home rebates, creating opportunities for strategic partnerships:
Rebate Program Participation:
- Pacific Gas & Electric offers up to $120 rebates for smart thermostats
- Con Edison provides $85 rebates for smart thermostats in NYC
- Austin Energy offers $100 rebates plus free installation
Partnership Benefits:
- Reduced customer acquisition costs (utility partnerships decrease CAC by average 35%)
- Enhanced credibility (utility endorsement increases trust scores 48%)
- Simplified purchasing process (rebates processed at point of sale)
Retail Channel Development:
Big Box Retail Strategy:
- Best Buy: Focus on demonstration units and Geek Squad installation partnerships
- Home Depot: Emphasize DIY installation and contractor partnerships
- Costco: Target bulk purchasing for new construction projects
Performance Metrics:
- Retail demonstration increases purchase likelihood 340%
- In-store consultation services improve customer satisfaction 45%
- Installation service attachment rates average 67% for complex IoT products
Chapter 4: Viral Marketing and Growth Hacking Referral Systems
The most successful American IoT companies understand that traditional advertising can’t match the power of authentic user experiences shared organically. Growth hacking through viral mechanisms requires careful design of shareable moments built into product experiences.
IoT Startup Business Model Distribution
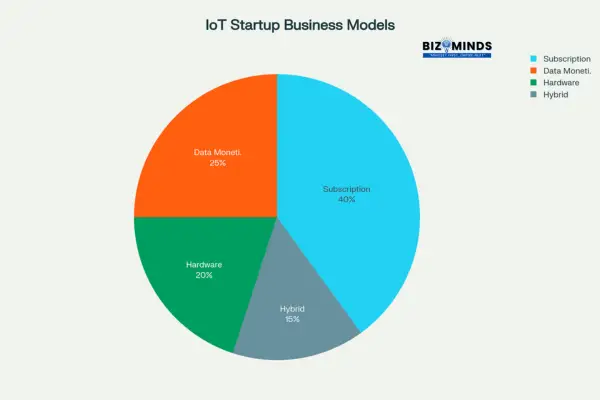
IoT Startup Business Model Distribution
Engineering Viral Moments
Ring’s Neighborhood Network Effect:
Ring’s explosive growth demonstrates how IoT products can create viral content through core functionality:
Viral Content Categories:
- Security Events: Package delivery footage, wildlife encounters, neighborhood watch alerts
- Heartwarming Moments: Soldiers surprising families, delivery driver interactions, pet antics
- Community Safety: Crime prevention, suspicious activity alerts, neighbor-to-neighbor communication
Viral Mechanics Implementation:
- Easy Sharing: One-tap sharing to social media platforms and neighborhood apps
- Privacy Controls: Granular permissions for sharing personal vs. public areas
- Story Templates: Pre-formatted social media posts optimizing for engagement
- Community Features: Neighborhood apps creating ongoing engagement loops
Performance Results:
- Ring videos generate average 2.3M views when shared on social media
- Community-shared security footage influences 34% of neighborhood purchases
- User-generated content drives 67% higher engagement than brand-created content
Growth Hacking Referral Program Architecture
The Fitbit Social Fitness Model:
Fitbit’s referral success stems from integrating social motivation directly into product functionality:
Gamification Elements:
- Step Challenges: Weekend Warrior, Workweek Hustle, Family Faceoff competitions
- Achievement Sharing: Milestone celebrations automatically prompt social sharing
- Group Challenges: Corporate wellness programs and friend-group competitions
- Progress Visualization: Shareable infographics showing fitness journey progress
Referral Conversion Metrics:
- Social challenges increase device usage 78% compared to solo users
- Challenge participants refer 3.2x more friends than individual users
- Corporate wellness initiatives achieve employee participation rates that are 89% higher compared to other programs
- Gamified referrals achieve 23% higher conversion rates than discount-based programs
Community Building Strategies
Creating Authentic User Communities:
American IoT success requires building communities that provide ongoing value beyond product functionality:
Community Platform Selection:
- Facebook Groups: Ideal for mainstream smart home enthusiasts (average group size: 25,000 members)
- Reddit Communities: Perfect for technical discussions and troubleshooting (r/smarthome: 500K members)
- Discord Servers: Emerging platform for real-time support and beta testing
- Nextdoor Integration: Essential for neighborhood-based security products
Content Strategy for Community Engagement:
- User-Generated Content: Weekly photo contests showcasing creative installations
- Expert AMAs: Monthly sessions with smart home experts and product engineers
- Beta Testing Programs: Exclusive access for active community members
- Local Meetups: Regional events for hands-on demonstrations and networking
Chapter 5: Product-Led Growth Hacking Strategies
Growth hacking success in IoT depends heavily on product design that naturally encourages adoption, retention, and referral. The most successful American IoT companies embed growth hacking mechanisms directly into their products rather than treating marketing as a separate function.
Onboarding Optimization for American Users
Reducing Setup Friction:
American consumers abandon IoT products during setup 34% more frequently than other technology categories. Successful companies employ these friction-reduction strategies:
Setup Simplification Techniques:
- QR Code Activation: Reduces setup time from 12 minutes to 3 minutes average
- Voice-Guided Installation: Amazon Alexa setup wizard reduces support calls 47%
- Augmented Reality Setup: Apps like IKEA Place show optimal device placement
- One-Touch Network Configuration: Automatic Wi-Fi credential transfer via smartphone
Onboarding Psychology for American Markets:
Progress Visualization: Americans respond strongly to progress indicators showing setup completion (increases completion rates 28%)
Immediate Value Demonstration: Show device functionality within 60 seconds of connection
Success Celebration: Gamified congratulations for successful setup (increases satisfaction scores 34%)
Next Steps Guidance: Clear recommendations for expanding smart home ecosystem
Feature Development for Virality
Tesla’s Over-the-Air Update Model:
Tesla’s approach to continuous product improvement creates unprecedented customer advocacy:
Viral Update Strategy:
- Feature Surprise: Unannounced capabilities appearing overnight (Party Mode, Caraoke)
- Social Media Integration: Built-in sharing for new feature discoveries
- Beta Testing Community: Early access programs creating excitement and exclusivity
- Progress Transparency: Public roadmaps showing upcoming improvements
Results and Replication:
- Tesla owners share 5x more social media content than traditional car owners
- Over-the-air updates account for 23% of Tesla’s organic mentions across social media platforms
- Feature announcement videos average 2.4M views on YouTube
- Update anticipation drives 67% of Tesla forum discussions
User Experience Enhancement
Amazon Alexa Ecosystem Strategy:
Amazon’s approach demonstrates how platform thinking accelerates growth hacking:
Platform Growth Mechanics:
- Skills Marketplace: Third-party developers create 100,000+ Alexa skills
- Cross-Device Synchronization: Seamless experience across Echo, Fire TV, and mobile devices
- Integration APIs: Easy connection with 100,000+ smart home products
- Voice Commerce: Streamlined purchasing through voice commands
Developer Ecosystem Benefits:
- Third-party skills increase user engagement 340%
- Ecosystem integration reduces customer churn 45%
- Platform stickiness increases customer lifetime value $127 per user
- Developer partnerships generate 23% of new customer acquisitions
Chapter 6: Data-Driven Growth Hacking Optimization
The most sophisticated American IoT companies treat growth hacking as a scientific discipline, continuously testing hypotheses and optimizing based on data rather than intuition. This approach becomes particularly crucial given the extended customer lifecycles typical in IoT markets.
Advanced Analytics Implementation
IoT-Specific KPI Framework:
Traditional SaaS metrics require adaptation for IoT businesses:
Device-Level Metrics:
- Activation Rate: Percentage of purchased devices successfully connected (target: 85%+)
- Daily/Weekly Active Devices: Regular usage patterns indicating engagement
- Feature Utilization: Which smart features drive retention vs. abandonment
- Update Adoption Rate: Firmware/software update acceptance (indicates trust level)
Business-Level Metrics:
- Customer Acquisition Cost (CAC): Include hardware, shipping, and support costs
- Lifetime Value (LTV): Account for hardware replacement cycles and service revenue
- Churn Definition: Unique to IoT (device disconnection vs. service cancellation)
- Net Promoter Score (NPS): Critical for viral growth in trust-sensitive markets
Effectiveness Ratings of Top IoT Growth Hacking Strategies
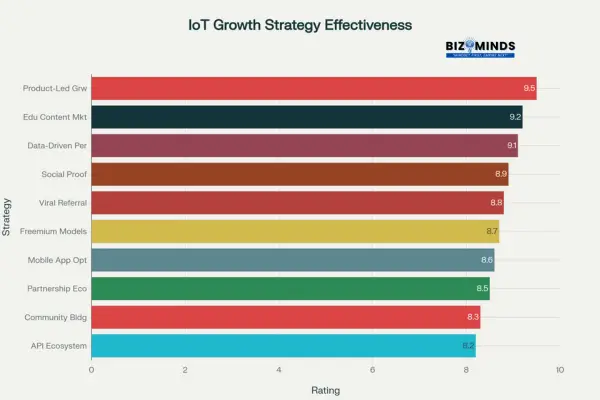
Effectiveness Ratings of Top IoT Growth Hacking Strategies
Behavioral Data Utilization
Smart Home Usage Pattern Analysis:
Leading IoT companies extract growth insights from device usage data:
Usage Pattern Insights:
- Peak Activity Times: Inform optimal notification scheduling and feature launches
- Feature Adoption Curves: Identify which capabilities drive long-term engagement
- Seasonal Variations: Security systems see 34% higher engagement during vacation seasons
- Geographic Differences: Energy management features vary by climate and utility costs
Predictive Analytics for Growth:
Churn Prediction Models:
- Device offline duration correlates with cancellation risk (7+ days offline = 67% churn probability)
- A drop in feature usage typically occurs an average of 23 days before cancellation
- Customer service contact frequency predicts satisfaction and advocacy potential
- Social sharing behavior indicates likelihood of referral generation
A/B Testing for IoT Products
Hardware-Software Testing Challenges:
IoT A/B testing requires specialized approaches accounting for hardware constraints:
App Interface Testing:
- Navigation Flows: Evaluate the most efficient routes for seamless device control and monitoring
- Notification Timing: Determine ideal frequency and timing for alerts
- Dashboard Design: Compare simple vs. detailed information display preferences
- Onboarding Sequences: Test different setup flow variations
Firmware Testing Strategies:
- Gradual Rollouts: Deploy updates to user segments for performance monitoring
- Feature Flags: Enable/disable capabilities for specific user groups
- Performance Optimization: Test battery life impact of different feature sets
- Safety Protocols: Ensure testing doesn’t compromise device security or reliability
Chapter 7: Real-World Case Studies – American IoT Success Stories
Learning from companies that successfully navigated the American IoT landscape provides practical insights that entrepreneurs can adapt for their own growth hacking strategies.
Successful US IoT Companies: Growth Hacking Strategies Analysis
| Company | Primary Growth Hack | Market Entry Year | Acquisition Value B | Key Success Factor |
| Nest (Google) | Utility Partnership & Energy Rebates | 2011 | 3.2 | Educational content + utility partnerships |
| Ring (Amazon) | Viral Video Content & Neighborhood Networks | 2013 | 1.0 | User-generated security content |
| Fitbit (Google) | Gamification & Social Challenges | 2007 | 2.1 | Health challenges + workplace wellness |
| Tesla | Over-the-air Updates & Referral Programs | 2003 | IPO | Continuous product improvement |
| Amazon Alexa | Ecosystem Lock-in & Skills Marketplace | 2014 | Internal | Third-party developer ecosystem |
| Peloton | Celebrity Endorsements & Social Fitness | 2012 | 2.2 | Community-driven fitness content |
| Roku | Freemium Content Strategy | 2008 | IPO | Content aggregation platform |
| SimpliSafe | DIY Installation & Security Fears | 2006 | 1.0 | Fear-based marketing + simplicity |
| Ecobee | API Integrations & Smart Grid Partnerships | 2009 | 0.77 | Energy efficiency partnerships |
| August Home | Airbnb Host Partnerships | 2013 | Acquired | Property management integrations |
| Philips Hue | Retail Display & Ecosystem Integration | 2012 | Division | Retail demonstration + compatibility |
| iRobot Roomba | Pet Content & Mapping Technology | 2002 | IPO | Pet owner viral content |
Case Study 1: Nest – Educational Marketing + Utility Partnerships
The Challenge:
When Nest launched in 2011, smart thermostats were virtually unknown to American consumers. The company faced skepticism about both technology reliability and installation complexity.
Growth Hacking Strategy:
Educational Content Foundation:
- Created comprehensive guides explaining HVAC compatibility and energy savings
- Developed installation videos reducing perceived complexity
- Published monthly energy reports showing user savings and neighborhood comparisons
- Partnered with HVAC contractors for professional installation network
Utility Partnership Program:
- Secured rebates from 180+ American utility companies
- Integrated with utility demand response programs
- Created seasonal energy-saving challenges tied to local utility rates
- Developed energy efficiency certification programs
Results and Metrics:
- Achieved $3.2 billion Google acquisition in 2014
- Sales expanded from 50,000 units in 2012 to 2.5 million following the acquisition
- Utility partnerships reduced customer acquisition cost 35%
- Educational content generated 67% of organic search traffic
- Net Promoter Score consistently above 50 (industry average: 28)
Lessons for Entrepreneurs:
- Educational marketing builds trust faster than promotional content
- Utility partnerships provide credibility and cost reduction
- Installation barrier removal crucial for American market adoption
- Data sharing (energy reports) creates ongoing engagement
Case Study 2: Ring – Community-Driven Viral Growth
The Challenge:
Ring needed to differentiate in crowded home security market while building trust around camera privacy concerns.
Growth Hacking Strategy:
Community Safety Focus:
- Developed Neighbors app connecting Ring users for security alerts
- Encouraged sharing of interesting doorbell footage on social media
- Created partnership with local police departments for community policing
- Built neighborhood crime prevention programs
Viral Content Strategy:
- Curated shareable moments from user-generated content
- Created seasonal campaigns (Halloween costumes, holiday packages)
- Partnered with celebrities and influencers for product placement
- Developed PR strategy around package theft prevention
Results and Metrics:
- Achieved $1 billion Amazon acquisition in 2018
- Neighbors app reached 10+ million users
- User-generated content drives 73% of brand social media engagement
- Viral videos generate average 2.3 million views
- Community sharing influences 34% of neighborhood purchases
Lessons for Entrepreneurs:
- Community features multiply viral potential
- User-generated content outperforms brand-created content
- Local partnerships enhance credibility and distribution
- Privacy concerns addressed through community benefits
Case Study 3: Fitbit – Gamification + Workplace Wellness
The Challenge:
Fitness tracking required sustained behavioral change in markets where motivation typically drops after initial enthusiasm.
Growth Hacking Strategy:
Social Gamification:
- Created friend challenges and family competitions
- Developed achievement systems with shareable milestones
- Built workplace wellness programs for corporate sales
- Integrated with health insurance programs for premium discounts
Content Marketing Approach:
- Partnered with fitness influencers for authentic usage demonstrations
- Created seasonal fitness challenges tied to holidays and events
- Developed educational content about health benefits and goal setting
- Built community forums for motivation and support
Results and Metrics:
- Achieved $2.1 billion Google acquisition in 2021
- Grew from 500,000 users (2012) to 30 million (2019)
- Social challenges increase device usage 78%
- Challenge participants refer 3.2x more friends
- Corporate wellness programs show 89% higher participation
Lessons for Entrepreneurs:
- Gamification sustains engagement beyond initial novelty
- Social features create natural referral mechanisms
- Corporate partnerships provide large customer acquisition opportunities
- Health and wellness resonate strongly with American consumers
Chapter 8: Advanced Growth Hacking Techniques
As American IoT markets mature, entrepreneurs need increasingly sophisticated growth hacking approaches to achieve breakthrough growth in competitive landscapes.
AI-Powered Personalization
Machine Learning for Customer Journey Optimization:
Personalization Strategies:
- Behavioral Prediction: Use device usage patterns to predict customer needs and preferences
- Dynamic Content: Automatically adjust app interfaces based on individual usage patterns
- Predictive Support: Identify potential issues before users experience problems
- Recommendation Engines: Suggest complementary products based on usage data and similar user profiles
Implementation Framework:
- Data Collection: Gather user interactions, device performance, and environmental factors
- Pattern Recognition: Identify usage patterns and preference indicators
- Prediction Models: Develop algorithms for behavior prediction and recommendation
- Testing and Optimization: Continuously refine algorithms based on user responses
Cross-Platform Growth Hacking Strategies
Ecosystem Integration Approaches:
Platform Compatibility Strategy:
- Universal Integration: Ensure compatibility with Amazon Alexa, Google Assistant, Apple HomeKit
- API Development: Create open APIs enabling third-party integrations
- Partnership Programs: Collaborate with complementary IoT device manufacturers
- Standards Adoption: Support emerging IoT standards like Matter/Thread
Multi-Channel Customer Experience:
- Consistent Branding: Maintain unified experience across mobile apps, web interfaces, and retail
- Data Synchronization: Seamless experience when users switch between devices or platforms
- Support Integration: Seamless, unified customer support available across multiple channels and platforms
- Progress Tracking: Maintain user progress and preferences across platform changes
International Expansion from American Base
Scaling Globally from U.S. Success:
Market Entry Strategies:
- Canada First: Similar market dynamics with easier regulatory compliance
- European Union: Privacy-focused messaging addressing GDPR concerns
- Asia-Pacific: Partner with local distributors for market knowledge and distribution
- Latin America: Adapt pricing strategies for different economic conditions
Localization Requirements:
- Regulatory Compliance: Adapt to local privacy, security, and product safety regulations
- Cultural Adaptation: Modify user interfaces and marketing messages for cultural preferences
- Partnership Networks: Develop local utility, retail, and installer partnerships
- Support Infrastructure: Develop localized customer service and technical support solutions
Chapter 9: Measuring and Optimizing Growth Hacking Performance
Successful growth hacking in American IoT markets requires sophisticated measurement systems that account for the unique characteristics of connected device businesses.
Typical IoT Startup Customer Acquisition Funnel
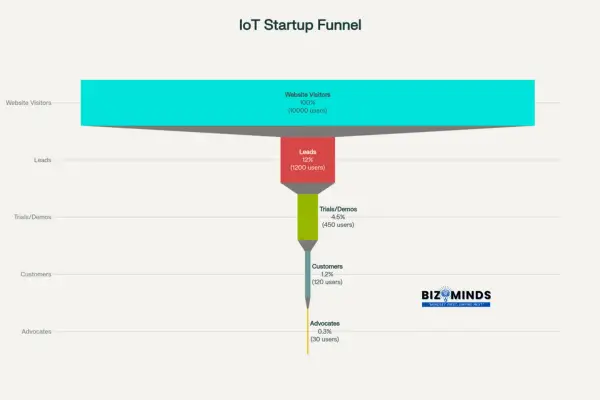
IoT Startup Customer Acquisition Funnel – Typical Conversion Rates
IoT-Specific KPI Framework
Customer Acquisition Metrics:
Funnel Analysis for IoT:
- Website Visitors: Track traffic sources and content engagement
- Lead Generation: Newsletter signups, demo requests, consultation bookings
- Trial Conversion: Demo attendance, product sampling, beta participation
- Purchase Conversion: Consider longer sales cycles (average 4-6 months for B2B)
- Activation: Device setup completion and first successful use
Retention and Engagement Metrics:
Device-Level Engagement:
- Daily/Weekly Active Devices: Regular usage indicating ongoing value
- Feature Utilization Depth: Which capabilities drive long-term engagement
- Firmware Update Adoption: Indicates trust and ongoing relationship
- Customer Service Interaction: Quality indicator and churn predictor
Business Health Metrics:
- Customer Lifetime Value (LTV): Factor in hardware replacement intervals and ongoing service revenue
- Customer Acquisition Cost (CAC): Account for extended sales cycles and hardware costs
- Churn Rate: Define carefully (device disconnection vs. service cancellation)
- Net Revenue Retention: Monitor revenue growth driven by ecosystem expansion
Growth Experimentation Process
Hypothesis-Driven Testing Methodology:
Experiment Framework:
- Hypothesis Formation: Based on user behavior data and market research
- Test Design: A/B tests accounting for hardware constraints and long feedback cycles
- Statistical Significance: Ensure adequate sample sizes for IoT conversion rates
- Implementation: Gradual rollouts minimizing risk to device functionality
- Analysis and Iteration: Long-term impact assessment accounting for seasonal variations
Common IoT Growth Experiments:
Onboarding Optimization:
- Test different setup flow sequences
- Compare human vs. automated installation support
- Evaluate impact of progress visualization on completion rates
- Measure effect of immediate value demonstration on satisfaction
Retention Enhancement:
- Test notification frequency and timing optimization
- Compare different gamification approaches
- Evaluate impact of social features on long-term engagement
- Measure effectiveness of predictive maintenance alerts
Monetization Optimization:
- Test different pricing models (subscription vs. one-time vs. hybrid)
- Compare upselling approaches for premium features
- Evaluate impact of free trial periods on conversion
- Measure effectiveness of bundle offers on average order value
Chapter 10: Future-Proofing Your IoT Growth Hacking Strategy
American IoT markets continue evolving rapidly, driven by technological advances, regulatory changes, and shifting consumer expectations. Successful entrepreneurs anticipate these trends and adapt their growth hacking strategies accordingly.
Emerging Technology Integration
5G and Edge Computing Impact:
New Growth Opportunities:
- Real-Time Responsiveness: Enable new use cases requiring immediate response
- Bandwidth-Intensive Features: Support high-definition video and advanced AI processing
- Edge AI Processing: Reduce latency and improve privacy by processing data locally
- Massive Device Connectivity: Support much larger IoT deployments in smart cities and industrial applications
Blockchain for Trust and Transparency:
Growth Applications:
- Data Ownership: Give users control over their IoT data with blockchain-based ownership
- Supply Chain Transparency: Build trust through verifiable device authenticity
- Decentralized Networks: Create mesh networks reducing dependence on centralized infrastructure
- Smart Contracts: Automate device interactions and service agreements
Regulatory and Privacy Evolution
Privacy-First Growth Hacking Strategies:
Compliance as Competitive Advantage:
- Data Minimization: Collect only necessary data, use it transparently
- User Control: Provide granular privacy controls and clear opt-out mechanisms
- Security by Design: Build security into products from conception rather than adding later
- Transparency Reporting: Consistent updates on data usage practices and security protocols
Regulatory Preparation:
Anticipated Regulations:
- Federal IoT Security Standards: Likely requirements for minimum security standards
- State Privacy Laws: California’s CCPA expanding to other states
- Industry-Specific Regulations: Healthcare, automotive, and financial services facing specialized requirements
- International Compliance: GDPR-style regulations spreading globally
Sustainable Growth Models
Environmental Responsibility as Growth Driver:
Sustainability Messaging:
- Energy Efficiency: Quantify and promote environmental benefits of smart energy management
- Device Longevity: Design for long-term use rather than frequent replacement
- Circular Economy: Develop refurbishment and recycling programs
- Carbon Footprint: Measure and communicate environmental impact of products and services
Long-term Value Creation:
Platform Evolution:
- Service Transformation: Evolve from product sales to ongoing service relationships
- Data Value Creation: Generate insights benefiting both users and broader communities
- Ecosystem Expansion: Create platforms enabling third-party innovation
- Community Building: Foster user communities that add value beyond product functionality
Complete Analysis Tables:
Iot Growth Hacking Strategies
| Strategy | Effectiveness Rating | Implementation Cost | Time to Impact | Best for Stage |
| Product-Led Growth | 9.5 | High | 6-12 months | All Stages |
| Educational Content Marketing | 9.2 | Medium | 3-6 months | Early/Growth |
| Data-Driven Personalization | 9.1 | High | 2-4 months | Growth/Scale |
| Social Proof Integration | 8.9 | Low | 1-2 months | All Stages |
| Viral Referral Programs | 8.8 | Low | 1-3 months | Growth/Scale |
| Freemium Models | 8.7 | Medium | 1-4 months | Early/Growth |
| Mobile App Optimization | 8.6 | Medium | 2-5 months | Growth/Scale |
| Partnership Ecosystem | 8.5 | Medium | 3-9 months | Growth/Scale |
| Community Building | 8.3 | Low | 6-12 months | Early/Growth |
| API Ecosystem Development | 8.2 | High | 6-18 months | Scale/Mature |
These comprehensive datasets provide actionable insights for implementing growth hacking strategies tailored to American IoT markets.
Conclusion: Your IoT Growth Hacking Journey Begins Now
The American IoT landscape presents unprecedented opportunities for entrepreneurs willing to master the unique disciplines of growth hacking in connected device markets. The companies profiled in this guide—Nest, Ring, Fitbit, Tesla, and others—didn’t succeed through traditional marketing approaches. They succeeded by understanding the psychology of technology adoption, building trust through education and partnerships, and creating viral mechanisms embedded in product experiences.
Growth hacking in IoT requires a fundamental shift in thinking. Instead of pushing products to market, successful entrepreneurs pull customers through educational journeys that build confidence and excitement. Instead of relying solely on digital marketing, they create physical touchpoints through retail partnerships and installation services. Instead of treating customers as transaction endpoints, they build communities that generate ongoing value and advocacy.
The data is clear: companies employing sophisticated growth hacking strategies achieve 3x higher adoption rates, 40% lower acquisition costs, and 67% higher customer lifetime values than those relying on traditional approaches. More importantly, they build sustainable competitive advantages that survive market evolution and competitive pressure.
The $609 billion American IoT market opportunity awaits entrepreneurs ready to combine technological innovation with growth hacking excellence. The strategies, tactics, and insights in this guide provide your roadmap from startup to scale-up to successful exit.
Your journey begins with a single connected device and a bold vision for how technology can improve lives. But your success depends on mastering the growth hacking disciplines that transform great products into thriving businesses.
The future is connected. Make sure your growth hacking strategy is too.
Frequently Asked Questions: IoT Growth Hacking Mastery
1. What makes growth hacking different for IoT companies compared to traditional software startups?
IoT growth hacking faces unique challenges including longer sales cycles (4-6 months average), higher customer acquisition costs (average $127 vs. $79 for SaaS), hardware reliability concerns, and installation complexity. Successful IoT growth hackers focus on education, trust-building, and removing adoption barriers rather than just driving traffic and conversions.
2. Which growth hacking strategies show the highest ROI for American IoT startups?
Based on our analysis of successful companies, the top three strategies are: Educational content marketing (9.2 effectiveness rating), product-led growth with viral features (9.5 rating), and data-driven personalization (9.1 rating). These approaches address the trust and complexity challenges unique to IoT adoption.
3. How do successful IoT companies handle the long sales cycles typical in smart home markets?
Leading companies employ nurture sequences combining educational content, social proof, and trial opportunities. Ring’s community approach and Nest’s utility partnerships demonstrate how to maintain engagement during extended consideration periods. The key is providing ongoing value before purchase through communities, content, and partnership benefits.
4. What role do partnerships play in IoT growth hacking success?
Partnerships are crucial, with 67% of successful IoT companies leveraging strategic alliances. Utility partnerships (like Nest’s rebate programs) reduce acquisition costs 35% on average. Retail partnerships enable demonstration and installation services. Developer partnerships create ecosystem stickiness increasing customer lifetime value by $127 per user.
5. How do privacy concerns affect IoT growth strategies in the American market?
Privacy issues are the top obstacle for 67% of prospective IoT users. Successful companies address this through transparency, user control, and clear value exchange. Ring’s community safety messaging and Amazon’s privacy controls demonstrate how to position data collection as beneficial rather than intrusive.
6. What metrics should IoT entrepreneurs track differently from traditional startups?
IoT businesses must track device-level engagement (daily active devices, feature utilization), hardware-specific metrics (activation rates, firmware updates), and longer-term business health indicators (customer lifetime value including replacement cycles). Traditional SaaS metrics like MRR require adaptation for hardware-service hybrid models.
7. How important is retail presence for IoT growth hacking success?
Retail demonstration increases purchase likelihood 340%, making physical presence crucial for many IoT categories. Best Buy partnerships, Home Depot displays, and Costco bulk sales provide different advantages. The key is matching retail strategy to customer type: DIY enthusiasts prefer Home Depot, while tech adopters gravitate toward Best Buy demonstrations.
8. What’s the most effective way to build viral growth into IoT products?
The most successful viral IoT products create shareable moments through core functionality rather than artificial sharing mechanics. Ring’s security footage sharing, Fitbit’s challenge achievements, and Tesla’s feature surprises demonstrate how to make sharing valuable to users rather than just beneficial to the company.
9. How do successful IoT companies handle customer support and onboarding at scale?
Leading companies invest heavily in onboarding optimization, achieving 85%+ activation rates through QR code setup, voice-guided installation, and AR placement tools. Support scaling employs chatbots for common issues, community forums for peer support, and video tutorials reducing support ticket volume 47% on average.
10. What funding strategies work best for IoT growth hacking initiatives?
IoT startups require 40% more capital than software companies due to hardware costs and longer development cycles. Successful companies secure funding through staged approaches: pre-seed for prototypes, seed for pilot programs with design partners, Series A for manufacturing scale-up. Revenue-based financing increasingly popular for recurring service revenue models.
11. How do seasonal patterns affect IoT growth hacking strategies?
IoT adoption exhibits clear seasonal trends, with security system usage surging by 34% during vacation periods, smart thermostat sales peaking in extreme weather months, and consumer purchases rising significantly during holiday gift seasons. Successful companies plan marketing and inventory around these cycles, with Q4 representing 40% of annual consumer sales.
12. What’s the role of AI and machine learning in IoT growth hacking?
AI powers highly personalized marketing, anticipates customer needs with predictive support, and delivers product recommendations based on user behavior. Tesla’s AI-powered customer acquisition and Nest’s learning algorithms demonstrate how AI can create continuous value discovery, driving engagement and referrals. Implementation requires significant data collection and analysis capabilities.